Imagine this…
You lock the front door of your house, but once someone is inside, they can go into any room, open any cupboard, or access anything — even your personal files. That’s how traditional IT security used to work. It trusted you completely once you were in.
But today, the world has changed — and Zero Trust Architecture is the new way to stay safe.
Let’s break this down in…
What is Zero Trust Architecture?
Zero Trust means exactly what it says:
Never trust, always verify.
Whether you’re inside the network, outside the network, working from the office, or logging in from your phone — the system doesn’t automatically trust you. It checks every time, for every access request, everywhere.
It’s like showing your ID every time you walk into a new room — even if you’ve already entered the building.
In tech terms, Zero Trust Architecture (ZTA) is a security model that assumes breach and verifies each request as though it originates from an untrusted network.
Why Do We Need Zero Trust?
Here’s the thing:
In today’s world…
- People work from home, coffee shops, or airplanes
- Apps are running in the cloud
- Devices are everywhere — laptops, mobiles, smart TVs
- Hackers are more clever than ever
The old castle-and-moat approach to security (protect the outside, trust the inside) doesn’t work anymore.
One weak link, like a stolen password or infected device, can give hackers access to the entire system. That’s dangerous.
So Zero Trust was born to fix that.
How Does Zero Trust Work?
Zero Trust isn’t a single tool or product.
It’s more like a strategy or mindset, made up of a few key principles:
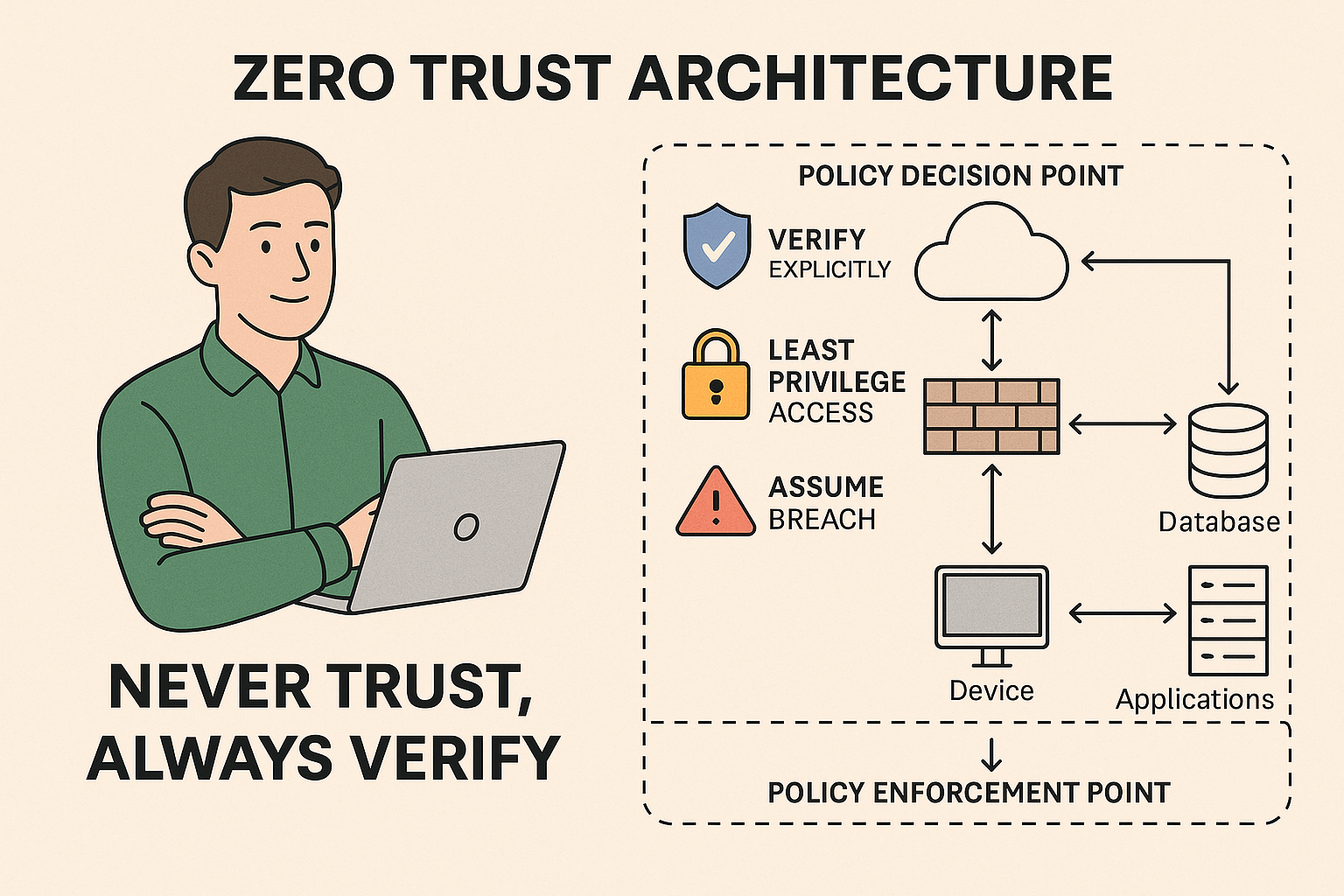
1. Verify Explicitly
Don’t assume the user is who they say they are.
Check every time.
- Use multi-factor authentication (MFA)
- Use biometrics, smart cards, or security keys
- Check location, device health, time of request, etc.
2. Use Least Privilege Access
Give people only the access they need, and nothing more.
Like a janitor getting keys only to the rooms they clean — not the CEO’s office.
This limits damage if something goes wrong.
3. Assume Breach
Design the system like it’s already under attack.
- Segment the network (so one infected device doesn’t spread malware everywhere)
- Monitor behavior constantly
- Log everything
If someone acts suspiciously, the system can flag or block them — even if they’re already logged in.
Real-Life Examples
- Google’s BeyondCorp: A famous Zero Trust model where employees can work securely from anywhere — without a traditional VPN.
- Banks & Healthcare Apps: Use Zero Trust to ensure only the right people can access sensitive info, and only for the right reasons.
- Cloud Services: AWS, Azure, and GCP now provide native Zero Trust features for securing workloads.
How to Start with Zero Trust?
If you’re part of a company or leading a team, here’s how to start:
- Know your assets – What devices, users, apps, and data do you have?
- Identify risks – Who has access to what? What’s critical?
- Implement MFA – Easy win. Add strong authentication.
- Segment networks – Stop lateral movement.
- Monitor everything – Use logs, alerts, and AI-based anomaly detection.
In a Nutshell
| Concept | Meaning |
|---|---|
| Zero Trust | Don’t trust anyone or anything by default |
| Goal | Stop unauthorized access, limit damage |
| Method | Always verify, limit access, monitor everything |
Final Thoughts
Zero Trust might sound like a buzzword, but it’s a real, practical, and necessary way to secure systems in a world where data is everywhere and perimeters don’t exist.
It’s not about trusting no one.
It’s about verifying everyone, every time — for your safety, and theirs.

Hi, this is a comment.
To get started with moderating, editing, and deleting comments, please visit the Comments screen in the dashboard.
Commenter avatars come from Gravatar.